This is a continuation of the previous post. For the impatient like me :) please refer source code here and download it.
https://github.com/maheshrajannan/NodeJs-SSL
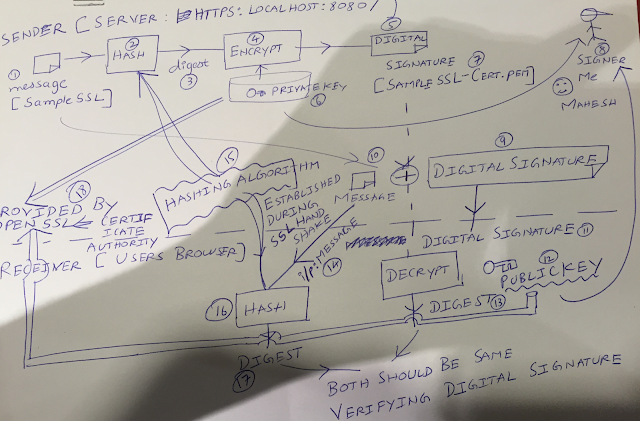
Please take a look at the diagram here.
A message (SampleSSL marked as (1) in the diagram below) is encrypted by a private key to produce digital signature (SampleSSL-Cert.pem marked as (7) ). I am the signer of this digital certificate (marked as (8) ) . The private public key pair is provided in this case by open SSL (marked as (18) ).
The digital signature (11) , is de-crypted by public key (12) and we have a digest at client (browser).
The input message (14) is hashed and we receive a digest (17) . Both should be same verifying the digest. Now the digital signature is verified and the owner (Me, Mahesh Rajannan) is verified and non repudiated ( i cannot deny it is not my signature) . The hashing algorithm (15) is established during SSL handshake, along with 10 other things.
A bunch of shared secrets are exchanged between sender (client browser) and receiver (server, localhost:8080) through asymmetric cryptography.Asymmetric cryptography is nothing but encrypt with public key and de-crypt with private key.
The source code for this is here. Please feel free to download and enjoy.
One shared secret is selected, through symmetric key cryptography the message (
https://github.com/maheshrajannan/NodeJs-SSL
Please take a look at the diagram here.
A message (SampleSSL marked as (1) in the diagram below) is encrypted by a private key to produce digital signature (SampleSSL-Cert.pem marked as (7) ). I am the signer of this digital certificate (marked as (8) ) . The private public key pair is provided in this case by open SSL (marked as (18) ).
The digital signature (11) , is de-crypted by public key (12) and we have a digest at client (browser).
The input message (14) is hashed and we receive a digest (17) . Both should be same verifying the digest. Now the digital signature is verified and the owner (Me, Mahesh Rajannan) is verified and non repudiated ( i cannot deny it is not my signature) . The hashing algorithm (15) is established during SSL handshake, along with 10 other things.
A bunch of shared secrets are exchanged between sender (client browser) and receiver (server, localhost:8080) through asymmetric cryptography.Asymmetric cryptography is nothing but encrypt with public key and de-crypt with private key.
The source code for this is here. Please feel free to download and enjoy.
One shared secret is selected, through symmetric key cryptography the message (
Hi from HTTPS) is exchanged , in an encrypted format between client and server,
using the shared key
References:
http://security.stackexchange.com/questions/20803/how-does-ssl-tls-work https://en.wikipedia.org/wiki/Transport_Layer_Security https://en.wikipedia.org/wiki/OSI_model https://en.wikipedia.org/wiki/Public-key_cryptography
On next post, Next some more improvements like
ReplyDelete1. jsLint for code formatting.
2. Mocha for test runner