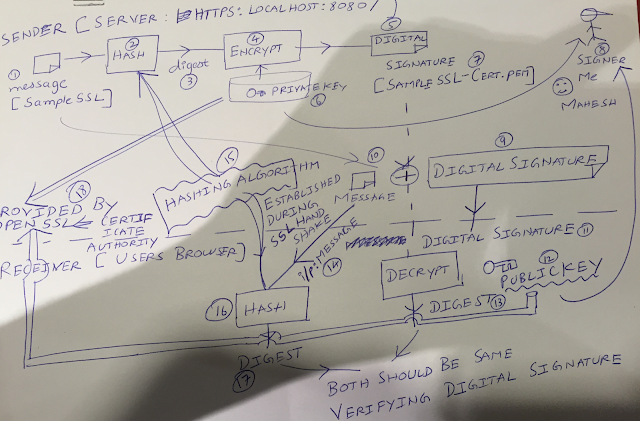
There are basically two basic strategies:
You can use "1", when dealing with large images or big sections of the page. Also in mobile devices, hide the less important devices by using angular tags.
The code is all on GITHUB. Use it to test and then follow it as applicable.
Simple to run,
1. Start Mongo DB.

2. Start the app. node server

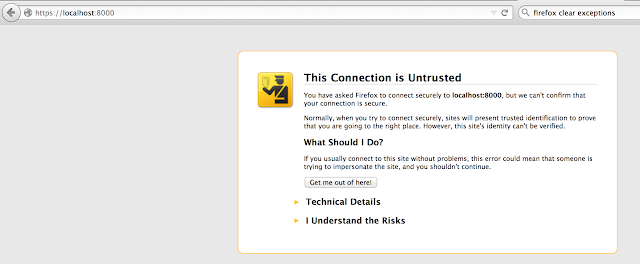
3. Go to http://localhost:8080

I downloaded a simple TODO app and injected adaptive-responsive tag.
This is how everything is organized (?) ...;) that is what i hate about angular...so called stipulated way of doing things...and it is so hard to represent.

- Use different views for each target device type.
- Use a single combined HTML file that uses CSS and media queries to hide those sections that should not be visible on a particular device. The sections that are not displayed still pull images and take up DOM processing time.
You can use "1", when dealing with large images or big sections of the page. Also in mobile devices, hide the less important devices by using angular tags.
The code is all on GITHUB. Use it to test and then follow it as applicable.
Simple to run,
1. Start Mongo DB.

2. Start the app. node server

3. Go to http://localhost:8080

I downloaded a simple TODO app and injected adaptive-responsive tag.
This is how everything is organized (?) ...;) that is what i hate about angular...so called stipulated way of doing things...and it is so hard to represent.